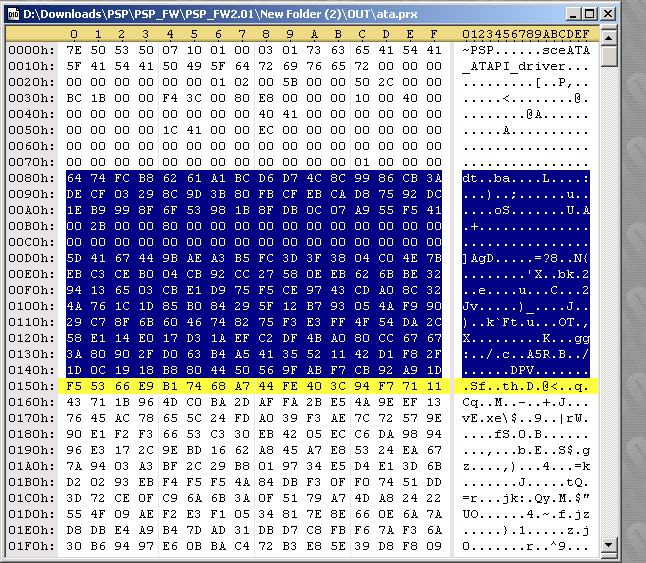
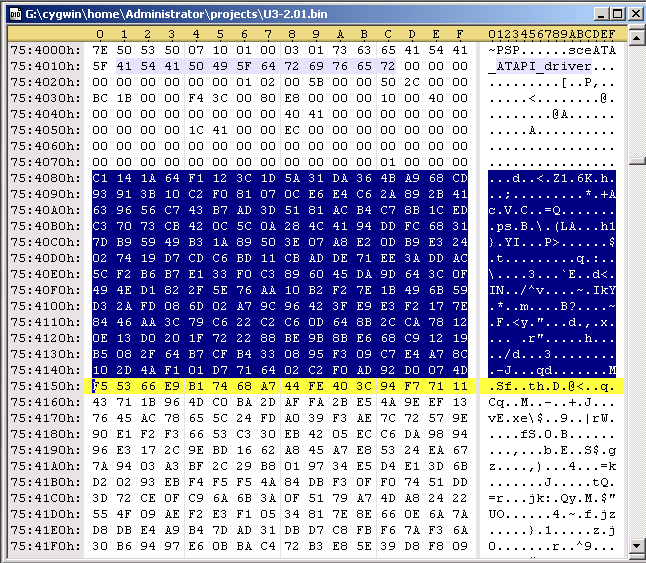
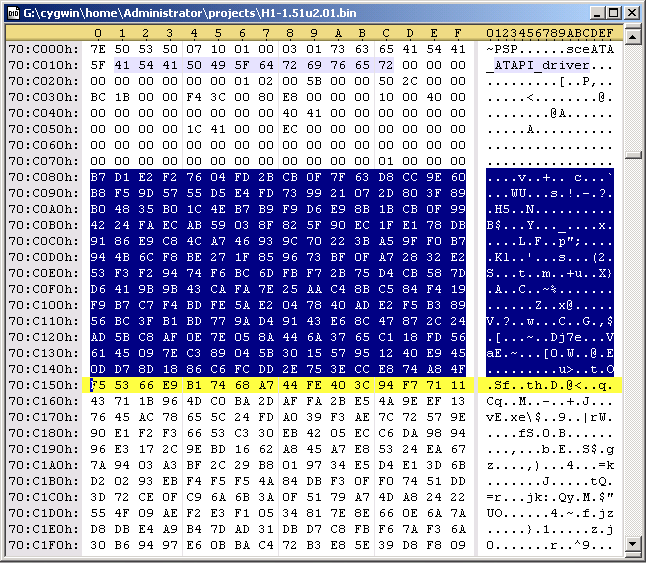
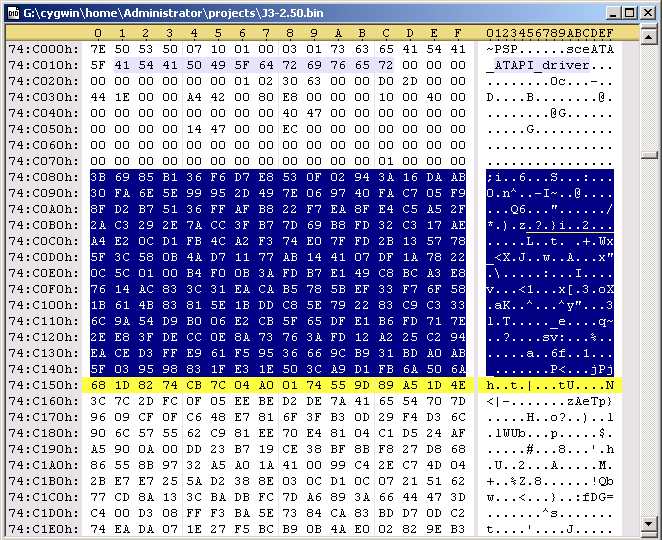
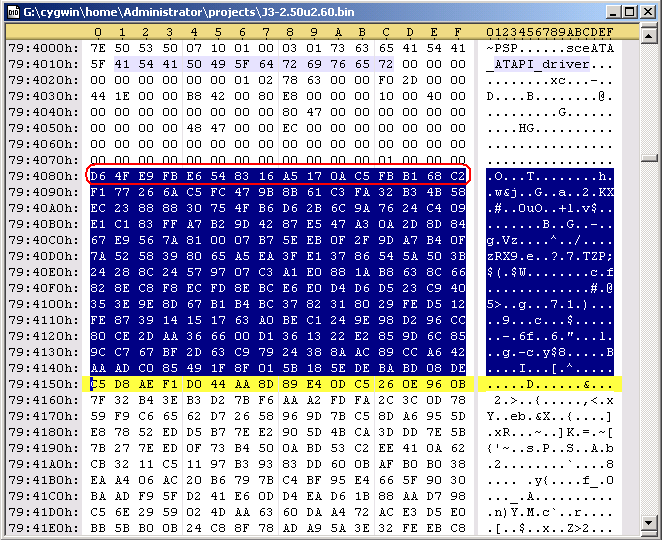
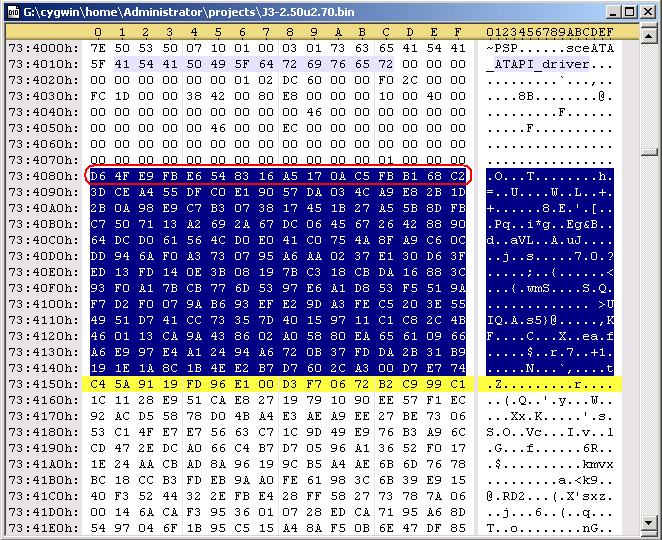
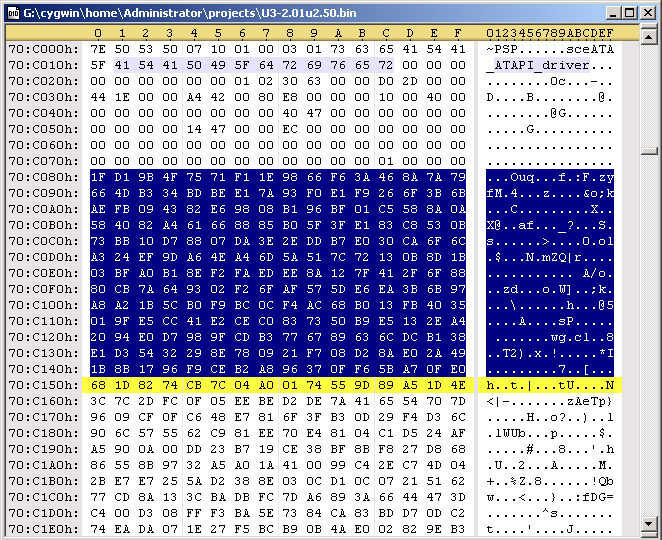
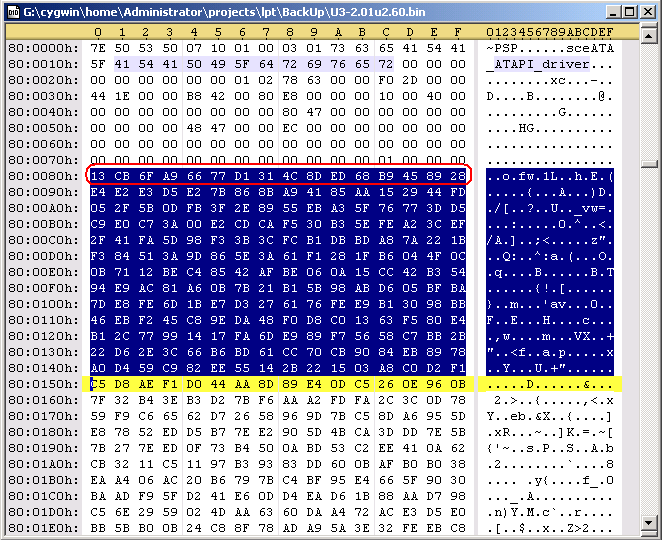
There are some parts of the header that can be edited. The following code is redoing the sha1 hash. Durring the decryption process, that PspPet is talking about, the keys are transformed by hw to what you'll see below in the code. With these new keys, you can edit the header of the prx file and redo the hash. Specificaly, you can edit the first 0x80 bytes in the file and from 0xE8 to 0x110.
Code: Select all
#include <stdio.h>
#include <string.h>
#include "sha1.h"
unsigned char
key0[20] = {0xBE, 0xF3, 0x21, 0x7B, 0x1D, 0x5E, 0x9C, 0x29, 0x71, 0x5E, 0x9C, 0x1C, 0x45, 0x46, 0xCB, 0x96, 0xE0, 0x1B, 0x9B, 0x3C},
key1[20] = {0x7A, 0x51, 0x59, 0xBA, 0xC5, 0xFB, 0xA5, 0x52, 0x2E, 0x14, 0x84, 0x82, 0xF9, 0x9D, 0x01, 0xB1, 0xE2, 0x23, 0x7C, 0x87},
key2[20] = {0x32, 0xA9, 0xFD, 0xCC, 0x76, 0x6F, 0xC0, 0x51, 0xCF, 0xCC, 0x6D, 0x04, 0x1E, 0x82, 0xE1, 0x49, 0x4C, 0x02, 0x3B, 0x7D},
key3[20] = {0xCA, 0xF5, 0xC8, 0xA6, 0x80, 0xC0, 0x67, 0x6D, 0x3A, 0x4D, 0x4F, 0x92, 0x6A, 0xA0, 0x7C, 0x04, 0x97, 0x02, 0x64, 0x08};
int main(int argc, char* argv[]){
FILE *f;
static unsigned char buf[10*1024*1024], header[0x150];//only 0x14C used
sha1_context cnx;
size_t size;
if (argc < 2){
printf("Usage: fixprxhdr.exe <file.prx>\n");
return 1;
}
if (fopen_s(&f, argv[1], "rb")){
printf("Could not open file '%s'\n", argv[1]);
return 2;
}
size=fread(buf, 1, 10*1024*1024, f);
fclose(f);
if (size<0x150){
printf("File '%s' is too small\n", argv[1]);
return 3;
}
memcpy(header+0x00, buf+0xD0, 0x80);
memcpy(header+0x80, buf+0x80, 0x50);
memcpy(header+0xD0, buf+0x00, 0x80);
switch(*(int*)header){
case 0:
memcpy(header+0x04, key0, 0x14);break;
case 1:
memcpy(header+0x04, key1, 0x14);break;
case 2:
memcpy(header+0x04, key2, 0x14);break;
case 3:
memcpy(header+0x04, key3, 0x14);break;
default:
printf("Unsupported version of the file: +0xD0: 0x%08X\n", *(int*)header);
return 4;
}
sha1_starts(&cnx);
sha1_update(&cnx, header+0x04, 0x14C);
sha1_finish(&cnx, buf+0xD4);
fopen_s(&f, argv[1], "wb");
fwrite(buf, 1, size, f);
fclose(f);
printf("PRX updated successfuly\n");
return 0;
}